By: Kirby Smith, Founder of SunKirb Ideas, LLC
No one is too busy to protect their passwords
My entire career has been involved with computer technology and digital devices. My past profession was as senior vice president of information technology for a mid-sized national company and now I own a business where I automate houses and set up smart homes. Both jobs have required me to set up and manage devices and network security for individuals and organizations. One area that has always stunned me is how lightly people treat the importance and protection of their passwords. Disproportionately, people live in ever-increasing fear of “hackers.” Just the mention of the word can cause people to rise up in outrage against companies blamed for not stopping the hackers. Before looking at why better password management should be higher on your list of online security priorities, let’s look at the reality of hackers and passwords.
What exactly is a Hacker?
Ironically, the word started off as something of a compliment. In the early days of computers, during the late 60s and 70s, computer technology started to move out of the military and corporations and into the hands of youthful people. These young pioneers could for the first time afford the technology to do something different. Many of these people would go on to form companies based on their creativity and perseverance. Some of these became familiar: Apple, Microsoft, Adobe, Intel, IBM, HP, Samsung (reborn 1960), Oracle, and Dell. When programmers would look at the accomplishments of others, knowing how much work it took to create something new or simplify something complicated, they equated it to cutting through a thick piece of wood or clearing a way through jungle growth. “They hacked away until they got through it!” If you developed a reputation for solving tech problems, you became known as a hacker.

Thieves followed the money
As the 80s rolled in, and more people started to use computers in the office, certain people found ways to exploit the system for personal gain or notoriety. The early 90s introduced the public to the Internet. Once the 2000s arrived, and people started to own more personal electronics, attention shifted to consumers instead of corporations to drive the economy. With the rise of Internet commerce, thieves adopted the tools and attitude of early developers. They used the same creativity and skills from the past to build theft technology and hacked away until they found cracks. For the first time, people started to think about internet security, and the word “hacker” entered the lexicon.
Imagine your online identity is like your house
Years later, what is our primary means of identity security on the internet? Usernames and passwords, the same system we had in the 60s. For organizations and companies, it is the easiest and cheapest solution” if it is used effectively. Better systems involve biometrics. Biometrics use sensors or cameras to measure people’s unique physical characteristics, analyze them, and create a unique key based on the data. For example, one can log in to a Windows 10 computer using their face, iPhones use fingerprints and face measurements, and some banks use speech patterns to identify you when you call in by having you speak random phrases. However, these systems are costly and to be cost effective they would require all companies to standardize on one method. For the time being, passwords will continue to be the primary identification system.

Easy to guess passwords: The equivalent of hiding your key under the doormat
Online thieves take the path of least resistance when they “break in.” They are not going to invest hours of time hacking into individual accounts (unless they personally know you). If one is going to hack in, they are more likely to go after large organizations holding the information of 100,000s or more users (such as the recent Wawa, Capital One and DoorDash breaches). This allows them to sell that information, make a quick profit, and reduce their risk of being caught since they haven’t directly stolen goods. Online thieves do know people’s habits. A large number of people have the following passwords, which don’t take a lot of hacking:
Top 10 Worst Passwords 2019 – (Read the full list)
- 123456
- 123456789
- qwerty
- password
- 1234567
- 12345678
- 12345
- iloveyou
- 111111
- 123123
These passwords are ranked as the worst because they are the most commonly used – making them easy to guess! Other common password mistakes include using your close family member’s name, your birthday, or names of things like your boat, team, or other information readily available on Facebook and other social media apps.
A simple trick for hackers is to go to a popular site like Facebook, scan for people who post pictures that practically advertise they have good income, pull their email from their site, and then run a program using that email to log into Facebook. The program will try common passwords, and if there is a hit, the program (often called a “bot”) will add the valid email/password combination to a list. This technique is called “Brute Force” hacking, and it is one of the least efficient methods for a hacker to use, but it works. For a hacker that knows who you are personally or is aware of your history, you are more likely to come under this attack.
Phishing
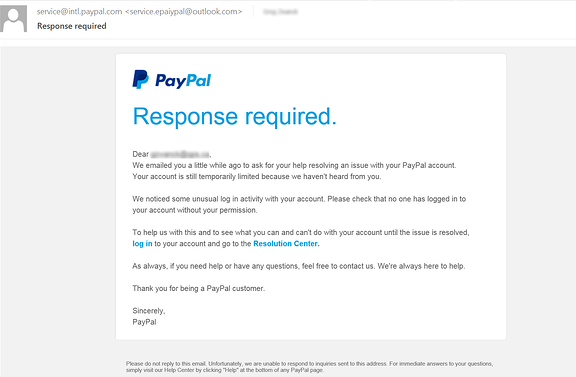
This is a classic example. At first glance, the email looks like it is from service@intl.paypal.com. Between the email address, logo, and similar font and format of legitimate emails from PayPal, one may feel a sense of urgency to act quickly by clicking on the links. However, take a closer look at the email address. When you receive an email, it is displayed in two parts: the actual email address and a display name. Most people are familiar with the actual email address layout, such as JPSmith@gmail.com. However, to make it easier to be recognized, the sender can supply a display name. So, the “From:” line in your email will often show “Johnny Smith < JPSmith@gmail.com >”. Online thieves know most people do not fully read the “From” line, so in our email example in the image it is actually showing “service@intl.paypal.com < service.epaiypal@outlook.com >”. Few people notice that the display name and actual email address don’t match – the actual email address uses the name “epaiypal” and is an Outlook email address (outlook.com is a free email service provider), not a PayPal email address (paypal.com).
If you click on the link, you will end up at a fake website which might have the address “HTTPS://epaiypal.us/user-login“. The site will look exactly like PayPal, except for the web address. It will likely ask for your login and you might type it in thinking the information is being sent to PayPal. After the login, it may have a pop-up that says, “Thank you for securing your account,” and you will go away thinking you stopped someone from hacking your account, when in fact you actually provided the thief with everything they needed to open your account and seize control.
Another insidious Phishing method used by online thieves involves social media, especially Facebook and LinkedIn. Often, this method is specifically designed for mobile users. For example, you might get a Facebook message from someone you know saying something like, “OMG! you’ve got to check out this hilarious video of a baby tasting ice cream for the first time!” Attached to the message is what appears to be a link to a YouTube video. You click on it and you may see a pop-up that appears to be from your phone (iOS or Android) which say, “Please confirm your intent to use Facebook to log in.” A box appears with an Apple logo and asks, “please provide your Apple login.” Not thinking about it, you provide your Apple login. A pop-up appears that says, “Error in display, please log back into Facebook”. You log back into Facebook and you are back to where you started. You give up and forget about it. Here is what happened:
Despite this appearing legitimate, almost everything is fake. You provided the thief with your Apple or Android login as well as your Facebook login. You also may have executed what is called a Trojan App that will log in to your Facebook, scan your contacts and friends, and send them the same message you received. Your friends will get a message from you and will likely fall for the same stunt.
While there are other online theft methods, Phishing is becoming the most prevalent because online thieves can get your passwords, use your credit cards, and spread malware to you at the same time.
Let’s go back to thinking about the security of your house. Imagine you are careful to lock the doors and windows. However, a stranger knocks on the door and when you answer, they tell you they are checking the neighborhood safety and want to borrow your key to inspect it. They wear a tag that says, “Neighborhood Security.” Because of the tag you feel safer and you hand them the key. They turn their back and do something then turn and give the key back to you. Neighborhood Security says thank you and leaves. It is highly unlikely you would do this in real life. However, people do this online every day.
With all the methods online thieves are using, and the fear they generate, we can go back to the original question, why aren’t more of us taking more care in choosing and guarding our login credentials? Sometimes it’s a lack of information, sometimes it’s about convenience, and other times it has to do with misplaced trust. Even internet-savvy people can make mistakes and overlook things. And with so many accounts to manage these days, the challenge is magnified because each one needs a unique password and security settings. Unfortunately, according to a recent study, 83% of users surveyed use the same passwords for multiple sites.
So, if the odds are that some of your credentials have been stolen (remember, many thieves sell the data before using it directly), and are floating around on the dark web, then why do we persist in using the same combination for almost all our personal, confidential, and financial accounts? The Wall Street Journal published an article with research about this:
…[I]n my research with Robert Otondo and Merrill Warkentin of Mississippi State University, we discovered there’s something else happening here: People have an emotional attachment to how they create their passwords. To most people, passwords aren’t just random. They’re personal.
The article goes on to point out two insights:
First is the “endowment effect.” It turns out that when we own things, we get attached to them. This, in turn, leads us to overvalue the owned item. My coffee cup is worth more than your coffee cup, simply because it’s mine. We become unwilling to swap it for another item with the same functionality, even if the replacement is superior to an unbiased observer. The second factor is what economist Dan Ariely calls “the IKEA effect”: We become inordinately attached to the things we create and, again, we overvalue them.
There are tons of websites and publications that recommend how to create passwords. However, we all resist the advice to some degree. Beyond crafting a better password (and making sure each account’s password is unique), there are two other simple things you can do to at least improve your online security:
- It can’t be emphasized enough to use what is called two-factor authentication (2FA). It is based on three generally recognized factors for authentication: something you know (such as a password or detail from your past, something you have (such as a cell phone for text/email, a computer you are already logged into, or a device/app called a token that creates random numbers and is synched to a service)), and something you are (such as your fingerprint). Two-factor means the system is using two of these options. For tokens, you may get it through text or Google or Microsoft Authenticator (free on Android and iOS). Twilio Authy, Duo Mobile, SAASPASS, and LastPass Authenticator, among others, all do the same thing on mobile and some desktop platforms, and most popular password managers all have 2FA by default. Watch this video to learn more about two-factor authentication.
- Use password storage apps, or at the very least a written list (kept in a safe private place), to note and manage your logins. I personally use the app called Keeper. Other top managers are 1Password, Dashlane, LastPass, and RoboForm. Most of the top ones run on all platforms (phones, tablets, and computers) and synch all your information between them. They have multi-levels of protections and can even create and manage passwords for you. They also integrate with biometric login systems including Microsoft, Apple iPhones/iPads and Droid. Read the list of the best password managers of 2020 with descriptions and ratings.
Phishing has become an industry where hackers now sell their services and tools. There is just too much money, vulnerable people online, and low risk for thieves to ignore the opportunities available to them. It might feel like experts are nagging you, but the danger is very real. Your best defense is to protect your passwords the way you would protect your physical keys. Below are links to other articles explaining how to protect yourself.
List of state by state cyber crime
How to recognize and avoid phishing scams
How hackers use emails to fool you with detailed examples and pictures

